What Exactly are Ghost Assets?
The term “ghost asset”is a bit of a catch-all. It could be:
- Unused accounts lingering in the system.
- Unmanaged servers gathering dust in a forgotten corner of the network.
- Software still technically active but no longer used by anyone.
Regardless of the type, they all represent a serious risk. As technology evolves with cloud computing, mobile devices, and the Internet of Things (IoT), the threat grows. Manual tracking methods simply can’t keep up.
The High Cost of Hidden Assets
Beyond the immediate security risk, ghost assets can lead to:
- Compliance headaches: During audits, if you can’t account for all your assets, you might face hefty fines.
- Financial losses: Unmonitored assets are prime targets for cybercriminals, leading to data breaches and millions in damages.
EnterCAASM: Your Ghost-Busting Toolkit
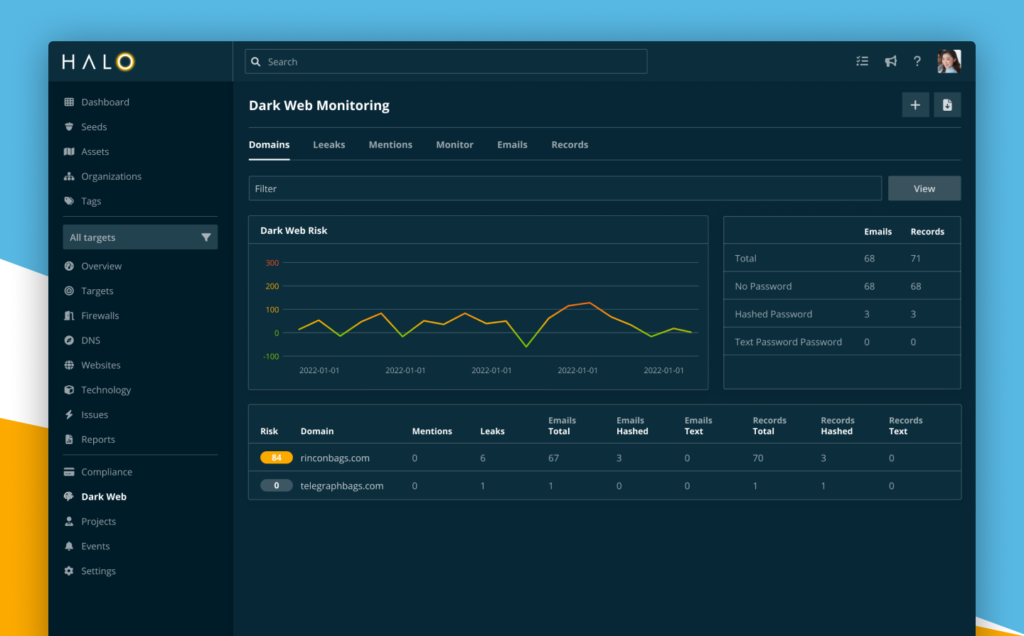
The first step to tackling ghost assets is gaining comprehensive visibility. CAASM platforms like Notus act as a flashlight, illuminating the hidden vulnerabilities within your network. Here’s how it works:
- See everything: CAASM integrates with all your systems, firewalls, and security tools to create a unified inventory of every device, account, and application across your network. No more blind spots!
- Focus on what matters: Not all assets are created equal. CAASM helps you identify your organization’s crown jewels, the critical systems and data that need the most protection. This allows you to prioritize security efforts effectively.
- Continuous monitoring: CAASM keeps your inventory up-to-date. As new devices are added or decommissioned, the platform automatically updates your records, preventing new ghosts from forming.
By proactively managing your cyber assets with CAASM, you can:
- Reduce your attack surface: Fewer hidden assets mean fewer entry points for attackers.
- Improve security posture: A comprehensive view of your network allows you to identify and address vulnerabilities more quickly.
- Ensure compliance: With complete asset visibility, you’re well-prepared for audits.
Conclusion
Visibility is viability in cybersecurity. Ghost assets pose a significant threat, but with CAASM, you can finally “bust” these ghosts and gain the control you need to secure your network. Remember, a well-lit network is a safe network. Don’t let hidden vulnerabilities haunt your organization – shine a light with CAASM and take control of your digital security.