Weekly Threat Intelligence Report
Date: April 29, 2024
Prepared by: David Brunsdon, Threat Intelligence – Security Engineer, HYAS
The HYAS Threat Intelligence team has been researching the potential relationship between two campaigns. Recently, thehackernews posted a description of zscaler’s research into a backdoored IP Scanner tool that uses DNS MX records for C2. From the actor’s email used to register the domains in the article, we used our HYAS Insight threat intelligence platform to identify hundreds of additional domain registrations not in the article. From some of these domains, we noticed additional C2 activity coming from the infrastructure, which could be the same actor, or an additional campaign also using the infrastructure.
For example, the domain adultgame[.]website was registered at Hostinger in 2022 by the wh8842480@gmail[.]com address from the research, and we have passive DNS records from 2023/11/04 to 2023/12/08 of the domain resolving to 35.186.223[.]180. In passive DNS we could identify other domains by that registrant email that also historically resolved to that IP.
During this same time frame, this same IP address has been used by a C2 operator to check their email and operate an Agent Tesla malware campaign.
Agent Tesla Overview
Agent Tesla is one of the most widespread information stealing malware variants in the cyber threat landscape. It is actively used in a wave of spear-phishing campaigns and other threat vectors to steal sensitive data such as usernames, passwords, and credit card information.
Organizations are recommended to maintain updated antivirus and antimalware solutions, provide continuous security training to employees, and use strong password policies. In addition, implementing a reliable spam filter and conducting regular network audits can help prevent and detect Agent Tesla infections.
Due to the adaptive nature of Agent Tesla, organizations are urged to maintain active security posture, remain updated on the latest intelligence, and implement proactive security measures like threat hunting and incident response plan.
Key Findings of Agent Tesla C2 Activity
2023/11/14 – 2023/11/16
Email server IP: 35.186.223[.]180 Actor email: silver.origin@ctlegal-hk[.]com Actor IP: 197.211.58[.]219 (Lagos, Nigeria) Actor Device User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Edg/120.0.0.0
Domain C2 IOCs:
www.abctech[.]life
www.solarpowerengage[.]life
C2 IPs:
69.57.161[.]215
By pivoting off the domain details of ctlegal-hk[.]com (the actor email domain), we can see it was registered by the following email address: zus.warehouses@gmail[.]com, from which we have identified a much larger campaign of Agent Tesla malware. This Agent Tesla campaign is currently ongoing and being investigated by our Threat Intelligence team.
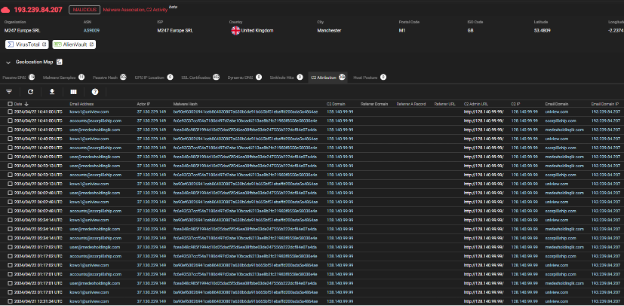
(example: ctlegal-hk[.]com>zus.warehouses@gmail[.]com>hhilton-sa[.]com>193.239.84[.]207>C2 Attribution)
Additional Agent Tesla C2 IoC
128.140.99[.]99
Agent Tesla SHA256 IoC
ba90ef60026941ceb864030807a630b6da91b665bf51ebaffd200ada5a4864ae
fc6e93537ccf54a7180d497d2abe10bcad6213ae8b2fc21983f8558e58030e4e
fcea048c985f1994d10d25dad5f5d6ea08fbbe03de247556b222dcf84e07a4da
zus.warehouses@gmail[.]com has registered hhilton-sa[.]com which currently resolves to an IP being used for an Agent Tesla C2 campaign.
This research demonstrates that an IP has been used by two recent campaigns during an overlapping time frame. It’s not uncommon for infrastructure to be used by multiple actors, however if additional correlation can be made between these two campaigns, then we could expand our knowledge of the campaign described in zscaler’s research.
Want to see some malware detonated? Join our upcoming webinar on April 30th at 10:00am PST / 1:00pm EST
Cyber Surveillance: Tracking New Malware Threats
Register here
Key Insights Into Agent Tesla Campaign Tactics
Labyrinthine C2 Infrastructure
The observed C2 infrastructure demonstrates a labyrinthine structure characterized by the utilization of multiple domains to orchestrate malicious activities. This intricate network complicates detection efforts and underscores the sophistication of the threat actor’s operational tactics.
Strategic Domain Selection
Domains such as “www.abctech[.]life” and “www.solarpowerengage[.]life” are strategically chosen to blend in with legitimate web entities while serving as conduits for malicious traffic. This deceptive tactic enhances the campaign’s stealth and resilience against detection.
Persistence and Adaptability
Our analysis reveals a persistent and adaptive threat actor presence, exemplified by the sprawling campaign infrastructure linked to the initial actor email domain. This indicates a sustained effort by threat actors to maintain operational continuity and evade detection measures.
Implications
Enhanced Detection Challenges
The complexity of the Agent Tesla campaign infrastructure poses significant challenges for traditional detection mechanisms. Security teams must leverage advanced threat intelligence and analysis techniques to effectively identify and mitigate threats emanating from this campaign.
Continuous Monitoring Requirements
Given the dynamic nature of this campaign, continuous monitoring of C2 infrastructure and domain registrations is imperative. Proactive threat hunting and real-time monitoring can help organizations stay ahead of emerging threats and mitigate potential risks.
Collaborative Defense Approach
Collaboration and information sharing among industry stakeholders are essential for combating the pervasive threat posed by the Agent Tesla campaign. By sharing insights and threat indicators, organizations can collectively strengthen their defenses and mitigate the impact of malicious activities.
Top Five ASNs Identified In HYAS Insight This Week
Noteworthy ASN detonations, including AS8968, AS44477, AS9318, AS216309, and AS216319, underscore the diverse landscape of cyber threats. Of particular concern is the prevalence of malware activity associated with these ASNs, such as their involvement in a wide range of malicious activities, the sophistication of threat actors operating within them, their global reach, dependencies on critical infrastructure, and challenges in attribution.
Key Challenges Posed
1. Association with Malicious Activities: These ASNs have been consistently linked to various malicious activities, including but not limited to hosting phishing websites, distributing malware, orchestrating ransomware attacks, propagating botnets, and launching distributed denial-of-service (DDoS) attacks. The persistence and diversity of these malicious activities make these ASNs particularly troublesome.
2. Sophistication of Threat Actors: The threat actors operating within these ASNs demonstrate a high level of sophistication in their tactics, techniques, and procedures (TTPs). They often employ advanced malware, evasion techniques, and social engineering tactics to bypass security measures and achieve their objectives. This sophistication makes it challenging for organizations to detect and mitigate threats effectively.
3. Global Reach: These ASNs have a broad geographic scope, providing internet and network services to customers across multiple regions and countries. As a result, the impact of malicious activities originating from these ASNs can be widespread, affecting organizations and individuals worldwide. The global reach of these ASNs amplifies the magnitude of the cyber threats they pose.
4. Challenges in Attribution: Attribution of cyberattacks and malicious activities to specific threat actors or entities within these ASNs can be challenging due to the use of anonymization techniques, proxy servers, and compromised infrastructure. This lack of attribution complicates efforts to hold responsible parties accountable and disrupt malicious operations effectively.
AS8968
AS8968, also known as BT Italia S.p.A., is an Autonomous System located in Italy. As its name suggests, it is primarily managed by BT Italia, a subsidiary of British Telecom (BT Group). The AS is known to have significant malware activity, which implies that it has been linked to several potentially harmful online activities and incidents. The high rate of malware activity on this ASN suggests either inadequate security measures or a potentially high volume of infected systems. Cybersecurity measures need to be robustly implemented and continuously monitored by the ISP to control and reduce the spread of malware.
Malicious Activities: Despite its legitimate business operations, AS8968 has been associated with various malicious activities, including hosting phishing websites, distributing malware, and serving as command and control (C2) infrastructure for botnets.
Impact: The presence of malicious activities within AS8968 poses a significant threat to organizations relying on its services, potentially leading to data breaches, financial losses, and reputational damage.
AS44477
AS44477 is the Autonomous System Number (ASN) assigned to a network operated by STARK INDUSTRIES, a suspected bulletproof host with connections to Russia. It’s not uncommon to see problematic traffic originate from STARK INDUSTRIES. From our data, this traffic is primarily Redline stealer, which steals personal browser data and joins victim devices to the ‘SPOO’ botnet.
Malicious Activities: AS44477 has been linked to sophisticated cyberattacks, such as ransomware deployments and data exfiltration attempts. Threat actors leveraging this ASN may target organizations across various sectors, exploiting vulnerabilities to achieve their objectives.
Impact: The involvement of AS44477 in malicious activities underscores the importance of robust cybersecurity measures and proactive threat detection capabilities to mitigate the risk of successful cyberattacks.
AS9318
AS9318 is the Autonomous System Number assigned to SK Broadband Co Ltd, a leading Internet Service Provider (ISP)based in South Korea. Significant malware activity related with this ASN suggests that infected devices connected to this provider may be contributing to cyber threats. It is important to note that the ISP may not necessarily be directly involved with this malicious activity. Such issues often stem from an often portion of the network being misused, typically as part of a botnet, without the provider’s knowledge. Ideally, they should take strict measures to identify and remove the compromised machines from their network.
Malicious Activities: AS9318 has been associated with the propagation of botnets, dissemination of malicious payloads, and hosting of malicious infrastructure. Threat actors leveraging this ASN may target both domestic and international entities, exploiting weaknesses in cybersecurity defenses.
Impact: The prevalence of malicious activities within AS9318 poses a significant threat to organizations relying on its infrastructure, highlighting the need for enhanced monitoring and mitigation efforts to protect against cyber threats.
AS216309
AS216309 is associated with TNSecurity, exhibiting an unusually high level of malware activity. However, abuse.ch warns that it should not be routed or peered at due to control by cybercriminals. Conflicting reports suggest origins in Germany and Russia.
Malicious Activities: AS216309 has emerged as a source of cyber threats, with indicators pointing to reconnaissance scans, exploitation attempts, and the establishment of malicious infrastructure. Threat actors may leverage this ASN to conduct targeted attacks against organizations worldwide.
Impact: The presence of malicious activities within AS216309 necessitates proactive defense measures and collaboration among cybersecurity stakeholders to mitigate the risk of successful cyberattacks and minimize potential impacts on affected entities.
AS216319
AS216319 is an ASN registered to CHROMIS LTD in the UK. HYAS has identified a significant amount of Amadey and Redline-based malware traffic going to ip:193.233.132.56 which is within that ASN. Although registered in the UK, IP probes are identifying that the traffic for that address is originating from Moscow, Russia. Further investigation demonstrated that CHROMIS LTD has provided a block of IP addresses (193.233.132.0/24) to ELITE-HOSTING-LTD in Russia.
Malicious Activities: AS216319 has been implicated in various cyber incidents, including distributed denial-of-service (DDoS) attacks, credential harvesting campaigns, and malware propagation. Threat actors leveraging this ASN may target organizations across multiple sectors, exploiting vulnerabilities to achieve their objectives.
Impact: The involvement of AS216319 in malicious activities underscores the importance of implementing robust cybersecurity measures and fostering collaboration across industry sectors to mitigate potential impacts and safeguard critical assets and operations.