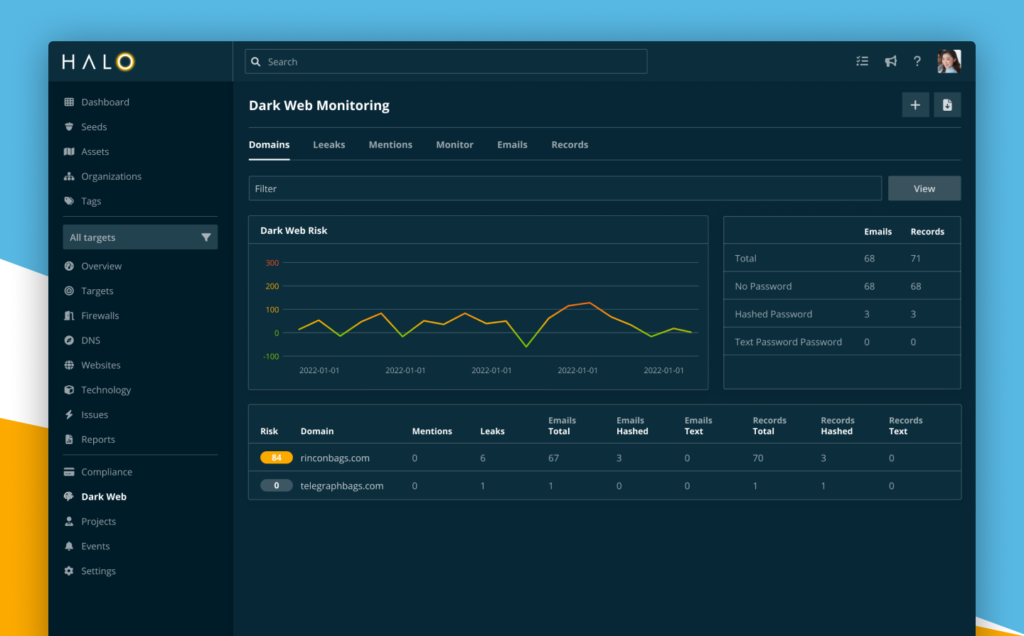
In the ever-evolving landscape of cybersecurity, recent data from the Ponemon Institute reveals that 53% of companies faced data breaches through third-party relationships in the last year. This alarming statistic emphasizes the pressing need for organizations to reevaluate their approaches to third-party risk management.
In today’s business environment, the widespread adoption of third-party services is nearly ubiquitous due to the myriad benefits they offer, including cost efficiency, specialized expertise, and operational streamlining. However, the inherent risks associated with these collaborations necessitate a paradigm shift in how organizations approach third-party risk management.
The modern business ecosystem is interconnected, with companies relying on external entities for various services, from IT support and cloud computing to supply chain management. This interconnectedness creates a complex web of potential vulnerabilities, making it imperative for organizations to fortify their defenses against cyber threats originating from third-party relationships.
Companies often face the dilemma of choosing between utilizing VDI infrastructure or dispatching laptops equipped with endpoint security tools. While VDI has traditionally served as a reliable solution for remote access, its inherent complexity and cost can sometimes outweigh its benefits. On the other hand, while shipping laptops is a viable option, it comes with significant expenses and time constraints. Not only does it demand a considerable budget, but the onboarding process is also not instantaneous; it typically takes months, factoring in shipping times and the acquisition of devices. Moreover, with privacy laws becoming increasingly stringent, installing a VPN or any other agent on a third-party contractor’s laptop for monitoring traffic is no longer a viable option.
Embracing Change: Say goodbye to VDI and hello to the Zero Trust Browser.
SURF’s Zero Trust Browser simplifies the onboarding process. Admins can send a link to download SURF; third-party users can install it and be onboarded to the protected work environment within minutes. The browser provides the same look and feel as the Chrome browser, without any latency like VDI would have, as it does not rely on any proxy or complex infrastructure.
As users open the browser, they are prompted for authentication as the first step, whether it’s through their Identity Provider (IDP) like Okta or local authentication. All predefined policies set by administrators are then applied to their browser.

Here’s where the policies come into play:
Data Loss Prevention (DLP) Controls: A standout feature of SURF’s Zero Trust browser is its robust DLP controls. This functionality is designed to thwart unauthorized data access and transmission, providing a critical layer of defense against potential breaches during third-party interactions. Admins can block, copy and paste from different pages, block printing, enforce PII masking, block screen capture and many others.
Web Filtering: The browser empowers organizations with granular web filtering capabilities, enabling them to control and restrict access to specific websites or based on category. This ensures that contractors only access authorized resources, mitigating the risk of potential security threats.
Secure Download Management: Download management actively monitors and controls file downloads. This prevents the inadvertent downloading of malicious files or unauthorized content, a crucial aspect of maintaining a secure digital environment.
Elevating Authentication with Transactional MFA: Security is further heightened with the inclusion of Transactional Multi-Factor Authentication (MFA). This advanced authentication method introduces additional verification steps during critical transactions, ensuring a higher level of identity validation and minimizing the risk of unauthorized access.
Safeguarding Against Keyloggers: In the battle against cyber threats, the Zero Trust browser incorporates keylogger prevention measures. This feature protects sensitive data entry and password inputs, fortifying the browser against potential malicious attempts to capture keystrokes.
Advanced Security Measures: ADMX and Malicious Processes Detection: The Zero Trust browser incorporates ADMX templates for centralized policy management, ensuring consistent and secure configurations. Additionally, advanced detection mechanisms identify and mitigate malicious processes, providing an extra layer of defense against evolving cyber threats.
Device Security Through Posture Checks: Recognizing the diversity of devices used by third-party contractors, the browser conducts posture checks to ensure compliance with security standards. This feature enhances overall device security, particularly crucial when dealing with a variety of devices for access.
Anti-Phishing Measures for a Deceptive-Free Environment: Phishing attempts remain a persistent threat in the digital landscape. SURF’s Zero Trust browser incorporates anti-phishing measures to identify and thwart phishing attempts, protecting users and the organization from deceptive schemes that could compromise sensitive information.
Conclusion
SURF’s Zero Trust browser emerges as a comprehensive solution for organizations seeking to enhance security in their collaborations with third-party contractors. Its array of features addresses the multifaceted challenges of modern cybersecurity, providing a secure, controlled, and seamless browsing experience for enhanced productivity and peace of mind. As organizations continue to navigate the dynamic landscape of digital collaboration, the Zero Trust browser stands as a beacon of trust and security.