Cybercrime is a rampant issue around the world, with the number of people affected, the amount of money lost, the costs of remediation, and the techniques used to compromise organizations constantly increasing.
Too many organizations have failed to keep up with the ever-evolving landscape of cybersecurity, and have suffered crippling data breaches and other kinds of attacks as a result.
Some of the strategies that cybersecurity analysts have traditionally employed undoubtedly leave room for error, and often result in fruitless labor that could have been allocated more productively.
Let’s take a look at some of the common mistakes made when managing an organization’s security posture and why they fail to provide adequate protection.
1. Focusing on internal assets at the expense of external assets
Organizations commonly have robust and expansive internal security controls and monitoring (though the IoT is beginning to change that). The problem is that assets outside the firewall often aren’t given the same attention and resources. Some organizations will muddle data from workstations together with data from public-facing websites, but that can create headaches and prevent the most likely-to-be-exploited entry points from being fully protected. Vulnerability assessment tools are often biased towards internal assets (which organizations generally have more of), so the best scanner for an employee workstation may not be the best for a mission-critical public web application server.
2. Trusting that all assets are known
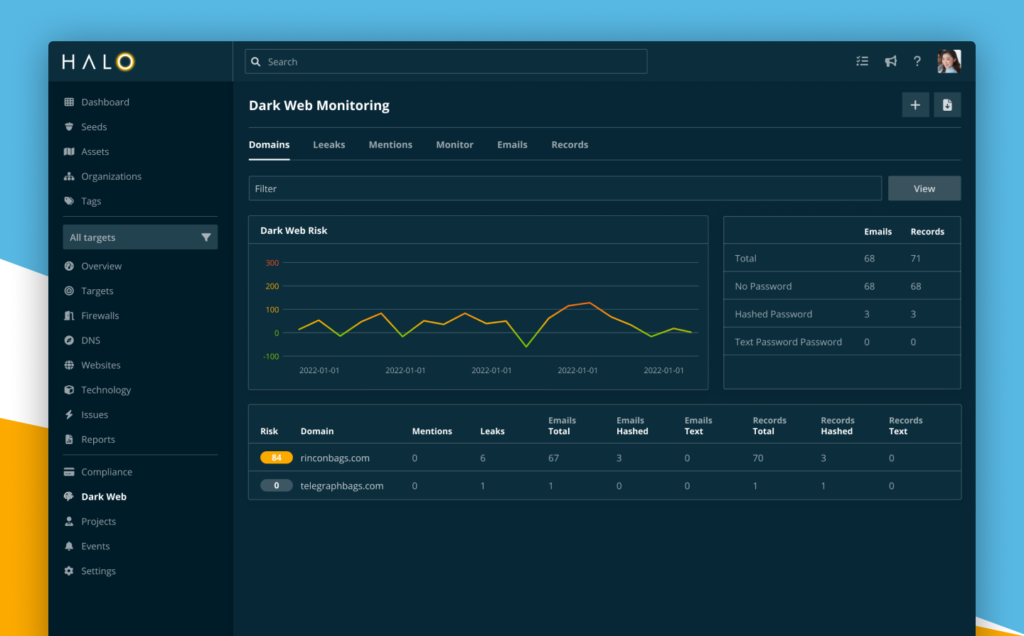
Ideally, cybersecurity stakeholders would be aware of every website and server belonging to their organizations, but that’s rarely the case. In our experience, discovery scans almost always uncover assets that our clients weren’t previously aware of because of things like shadow IT and merger acquired assets. If you aren’t constantly analyzing what’s on your attack surface, risk is left on the table.
3. Measuring success on the quantity of vulnerabilities found and remediated
Some analysts like to focus on finding every possible vulnerability and issue within their organization, and look at the number of those remediated as a measurement of their success. Crossing off false positives and patching high quantities of issues can feel good, but time and resources are better spent on finding and fixing the issues that pose the greatest risk, rather than smaller issues that pose little risk.
4. Relying on point-in-time risk analysis and penetration testing
Risk analysis and penetration testing are important components of a comprehensive cybersecurity program. But if you’re not doing these on a regular basis, you’ll only be able to fix the issues found at that point in time, leaving your business vulnerable to risks that emerge thereafter. Services that identify areas of risk in real-time, like Halo Security’s attack surface management solution, can help organizations stay up to date on present and future threats.
5. Reducing assets exclusively
Traditional attack surface management often focuses on simply trying to eliminate the number of exposed assets within an organization. And while of course it is valuable to clear out assets that aren’t viable, this strategy can only go so far when you have a growing business that utilizes the internet.
If your current approach to cybersecurity leaves room for risk, it may be time to steer in a new direction.
Halo Security helps businesses of all sizes manage their attack surface and improve their security posture with a systematic, risk-based approach, whether they have 10 assets or 10,000. Schedule a free consultation today to see how a new security testing strategy could benefit your organization.